The 3 Elements of Cybersecurity: You Need Them All
There are 3 elements of cybersecurity. Do you know them? If not, you're at risk of exposure to the evolving digital risk landscape. Read more to find out.
Protect your business today!
Get a QuoteThere are 3 elements of cybersecurity. If you’re missing any
one of them, you could be making yourself an easy target for data thieves
and likely purchasing a one-way ticket to a world of hurt.
You might be wondering if this is something you really need to worry about. Well, Embroker asked business owners that exact thing. In their recent Cyber Risk Index Report, founders in 2022 admitted that they were much more worried about cyber attacks than they were in the previous year.
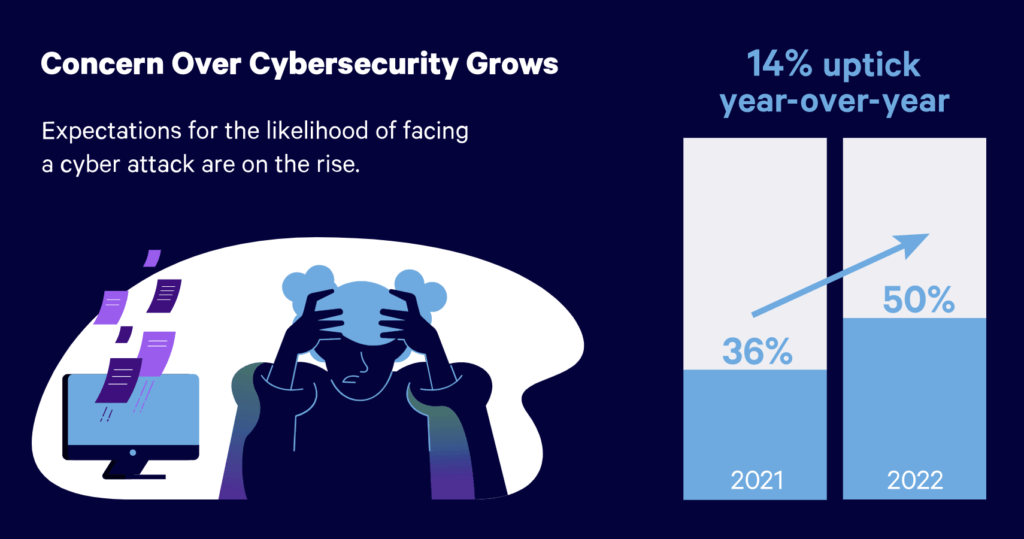
Check out the full report for more details.
The 3 elements of cybersecurity are prevention, detection, and response. Within each of
these are specific steps you need to take to give yourself the best chance of
foiling cybercriminals who want your data—specifically, your client’s names,
addresses, Social Security numbers, bank account details, taxpayer
information, and sundry other secrets, including confidential
correspondences, statements against interest, and your pre-trial strategy
notes.
These are data you have a duty to safeguard, and breaching that duty
carries with it some unpleasant consequences. For example, it could cost you
a ton of money to pay out to injured clients. It could cost you your reputation
since a data breach isn’t anything you can hide—when it happens, you have
a moral obligation and almost surely a statutory one as well to publicly
disclose that confidential data entrusted to you have been compromised.
And a breach of the duty to safeguard client information as outlined in Rule
1.6(c) of the American Bar Association’s Model Rules of Professional
Responsibility could cost you your law license, either temporarily or
permanently.
So, without further fanfare, let’s look at the three components of
cybersecurity. We begin with arguably the most important of the 3 elements of cybersecurity: the element of prevention.
The 3 Elements of Cybersecurity: Prevention
When it comes to cybersecurity, the old saying about an ounce of prevention
being worth a pound of cure is absolutely true. Indeed, the most cost-
effective (and sanity-sparing) way of saving yourself from the consequences
of a cyberattack is not allowing it to take place.
Here’s what you should do if you want to prevent a cyberattack.
The first order of business—and this is super-important, which is why I’m
telling you about it right up front—procure a cyber-insurance policy. Do not
rely on any other form of insurance to protect yourself from the
consequences of a cyberattack. Cyber insurance is the only type of coverage
that will keep you from going under financially due to a data breach.
Granted, this insurance won’t stop hackers and other malefactors from
successfully dipping their sticky fingers into your jar of honey-sweet data,
but it’s a vital preventive measure, nonetheless (even for small businesses).
Next, get in the habit of being stingy with the amount of information you
share online. The less you share, the better because you never know who
might lurk in the virtual shadows to spy on your email exchanges and
website visits. Say “no thanks” when the little popup on your screen invites
you to share location data. Decline the offer to accept cookies, if possible.
Frequently run security scans of your systems. Ensure your computer’s
operating system, browsers, programs, and everything else is up to date.
That means you need to have the latest version of each installed. You also
should have the newest security patches in place. Cobwebbed software is
usually a serious vulnerability.
From there, apply a scrutinizing eye to all your passwords. If you’re using
weak passwords, stop. Swap them out for new and strong passwords. A weak
password is something along the lines of 123456. A strong password
contains a randomized mix of upper- and lower-case letters plus numerals
and special characters. Your best bet is to acquire a password management
app—it’ll automatically create hyper-strong passwords, and no two will ever
be the same. The password manager will also remember each one for you,
so you’ll never need to write them down. One more thing: activate multi-
factor authentication (MFA), which will require you to provide at least one
additional piece of evidence to prove you are who you claim to be (and not
some hacker who managed to pilfer your password) before it will roll out the
welcome mat and grant you access.
Start using a virtual private network (VPN) whenever you hop onto the
internet, whether to send an email or visit a website. Backup your files
frequently: once a day is good, once a minute is ideal (there are security
packages you can obtain that will automatically backup your files for you
and, as a bonus, encrypt them—encryption being an outstanding way to
frustrate cybercriminals).
Finally, to really get a grasp of how to prevent a cyber attack (as well as the 3 elements of cybersecurity) sign up for cybersecurity training—not just for yourself but everyone
in your office. With training, you will learn how to spot phishing scams, email
compromise attacks, and other forms of trickery designed to lull you into
giving away your access credentials or unwittingly initiating a deadly
download of viruses or malware. Training will also instill in you and your
team numerous good habits, such as not sharing personal passwords and
never leaving the desk without first locking the computer screen.
The 3 Elements of Cybersecurity: Detection
Cyberthieves are so good at what they do that it typically takes the victim
200 days to realize a data breach has occurred. It takes that long because
the average victim isn’t sufficiently vigilant in watching out for the signs of a
cyberattack.
Therefore, you should review your bank and credit card statements regularly.
Also, take a more frequent look at what the credit bureaus (Equifax,
TransUnion, and Experian) are saying about you—for example, are they
reporting that you’ve taken out a loan you know nothing about or have
moved to a new address in a location you’ve never so much as visited?
Those are signs you’ve been data breached.
Pay closer attention to how your computers and mobile devices are
behaving. Be suspicious if they’re suddenly running slow or doing
inexplicable weird things—chances are they’re infected with viruses or
malware, or perhaps a hacker has burrowed in and taken control.
Another sign of a cyberattack is that you’ll start to receive emails seemingly
from colleagues and others with whom you have a trusted relationship.
These emails will appear authentic but are actually from cybercrooks doing a
really good impersonation of your colleague. The giveaway that they’re
frauds is that you’ll be asked to share your login credentials with them or to
pay this invoice for something you know you paid months ago.
The 3 Elements of Cybersecurity: Response
The faster you shift into response mode after a cyberattack is detected, the
better off you will be. It will help if you took time during the prevention phase
to create an action plan detailing your response so that you and your team
know exactly what to do and in which order. No guessing, no running around
with your hair on fire.
In the event of a breach, immediately contact your cyber-insurance company
so they can begin coming to your aid with the cash and other support you
will need to avoid financial and reputational ruin.
This next step, some say, should be performed before you contact your
cyber-insurance company, while others say to do it right after. Either way,
you need to seal off your systems from the outside world so that no further
data loss can occur. That means cutting your internet connections and killing
your network feed. Please don’t go back online until a computer security
specialist or IT-managed service provider sift through your systems with a
fine-tooth comb to determine how you were breached and then plug that
hole.
Then you must begin the process of notifying all affected parties—first and
foremost, your clients. You have to tell them that you were the victim of a
data breach and explain how that event impacts them. It’s a smart move to
include in that notification a promise to pay for credit monitoring so that
those impacted by the breach will be timely alerted if their stolen personal
information is subsequently used to engage in financial crimes.
The rest is pretty straightforward. Contact law enforcement to let them know
what happened. Ditto Social Security, your bank, and your creditors so they
can put holds on your accounts and issue new ones.
And there you have it. The 3 elements of cybersecurity; are
prevention, detection, and response. You need all three in place if you want
to come out on the other side of a data breach, a phishing scam, a
ransomware attack, or anything else cyber-based with your finances, client
roster, brand reputation, and possibly even your law license intact.
Tom Lambotte
CEO of Boba Guard
This article was provided by Tom Lambotte, a cybersecurity expert who has been in the tech support industry for over a decade. Tom founded BobaGuard in 2019, which offers turnkey solutions to solo lawyers and small-to-medium law firms. In addition, Tom is also the CEO and Founder of GlobalMac IT, an established managed service provider specializing in serving lawyers nationwide who use Macs by implementing his Proven Process™.

